 Matteo Conta - 15 مايو, 2019 - 9 ’ read
Matteo Conta - 15 مايو, 2019 - 9 ’ readImagicle applications security: vulnerabilities and threats mitigation.
If you work with software solutions like I do, you are probably well aware of the importance of online security. You may think you have it handled, but like many other companies, there probably hasn’t been enough done to secure your web applications. Scroll through the article, explore the most common vulnerabilities and learn some basic method of threat mitigation we’ve developed at Imagicle to keep malicious hackers at bay.
Getting started with web application security.
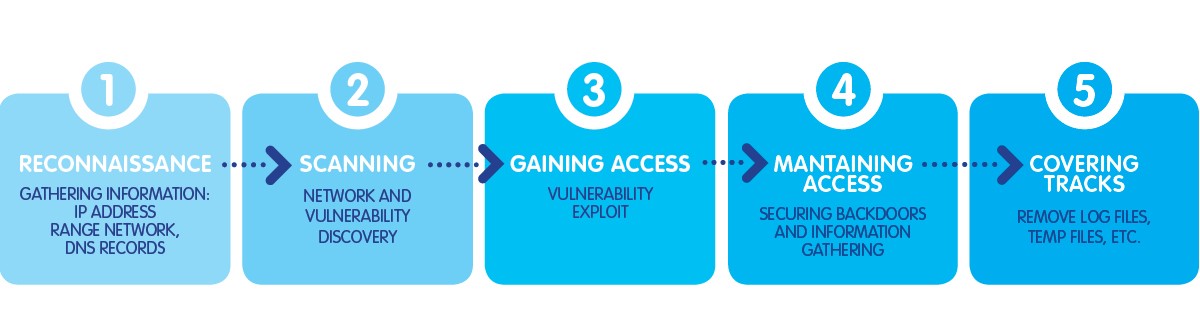
OWASP Top 10 web application security risks.
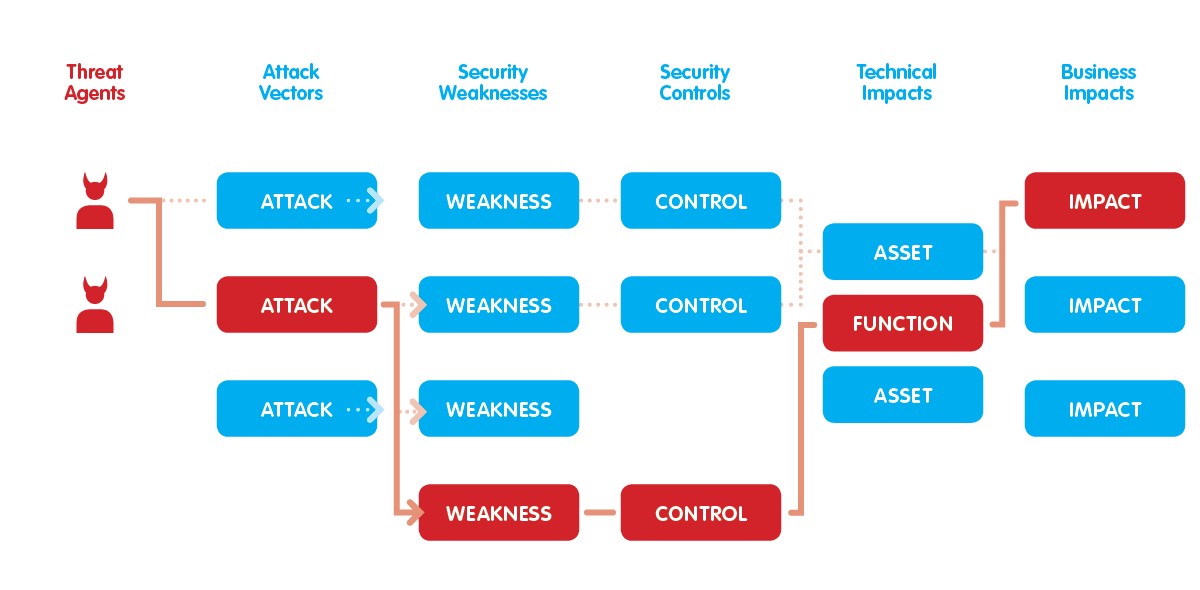
Use cases: securing applications and data.
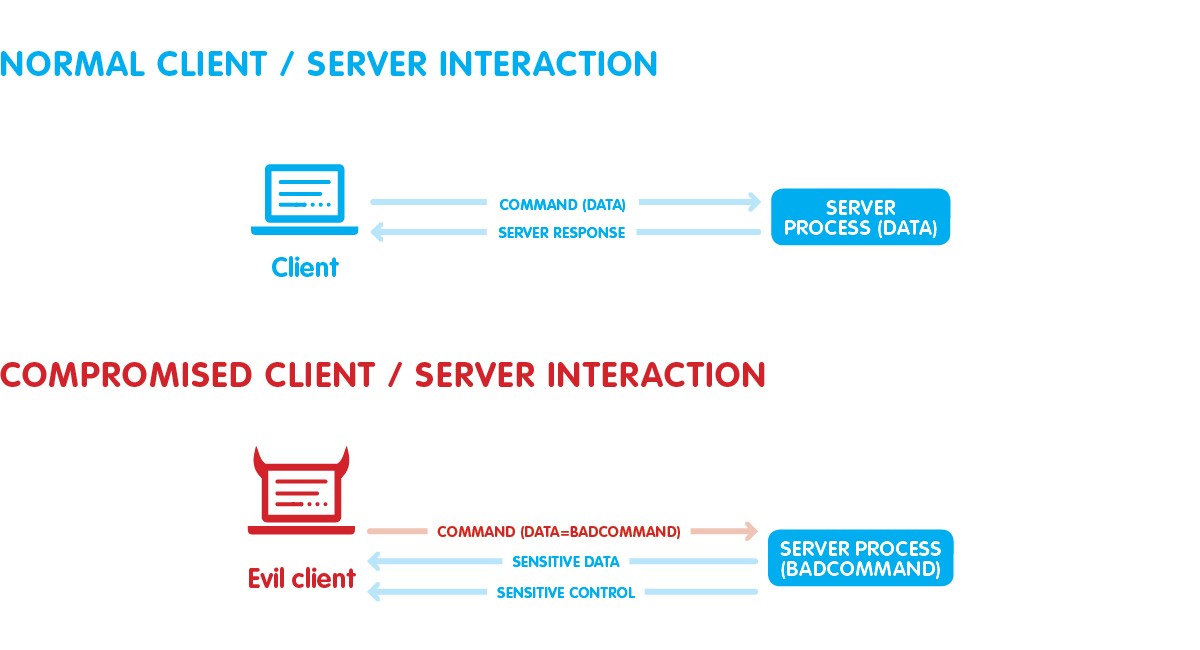
Command injection
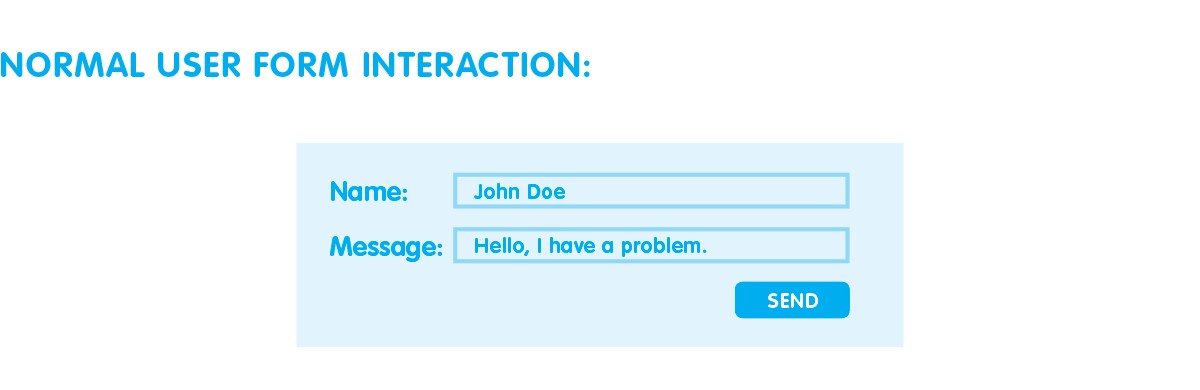
Cross-site scripting
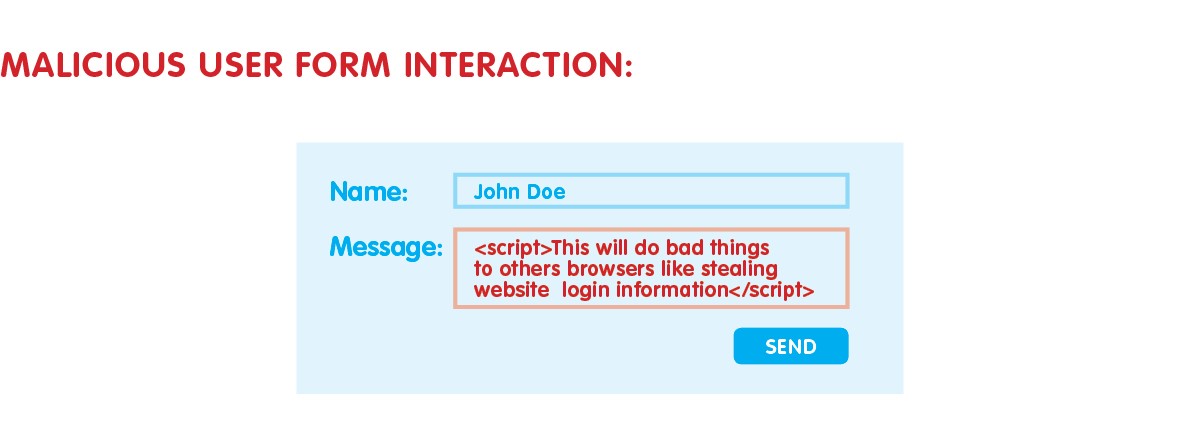
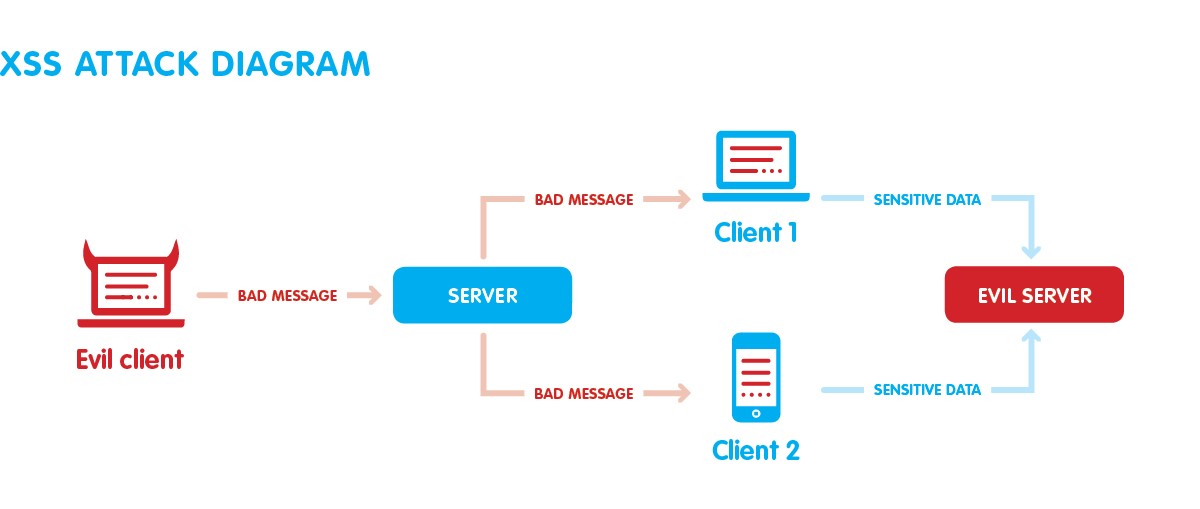
Imagicle application security best practices
Hack yourself.
Spread knowledge.
Use a web vulnerability scanner.
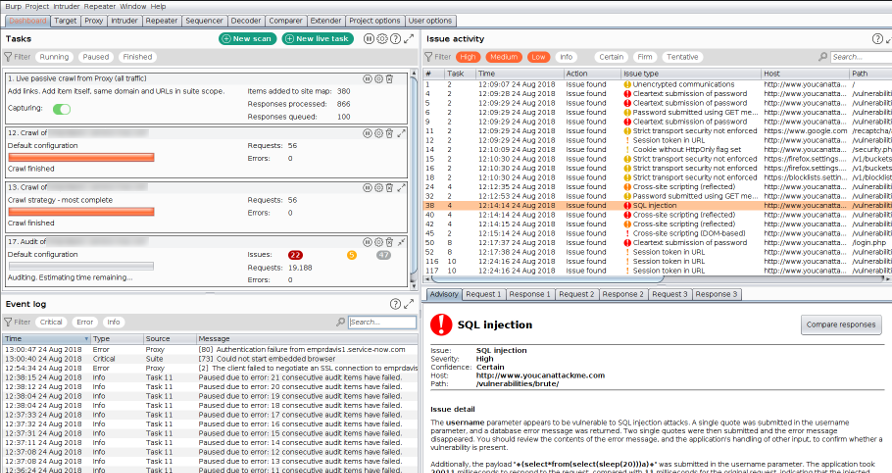
Pro tip. Let’s go to the gym
Conclusions.
At Imagicle we work every day to make your applications safer, investing in research and progress to develop effective methods to be able to fight the highest possible number of threats.
What we do is trying to make a field of vague security requirements and unknown threats a bit less vague and better known.
You might also be interested in…
-
Products BlogCloud or Dedicated Cloud. What’s best?Cloud or Dedicated Cloud. What’s best?You're migrating to the Cloud and you need to choose between a public or private instance? This article will help you.
-
Products BlogImagicle Attendant Console for Webex Calling: the operator console that was missing.Imagicle Attendant Console for Webex Calling: the operator console that was missing.Discover a new native integration. Attendant Console is fully compatible with all Cisco platforms!
-
Products BlogVoice Analytics: designed for your privacy and security.Voice Analytics: designed for your privacy and security.Voice Analytics handles a variety of sensitive, personal data. Learn why you can trust it to do so, any time, anywhere.
Products Blog
Cloud or Dedicated Cloud. What’s best?
Cloud or Dedicated Cloud. What’s best?
You're migrating to the Cloud and you need to choose between a public or private instance? This article will help you.
Products Blog
Imagicle Attendant Console for Webex Calling: the operator console that was missing.
Imagicle Attendant Console for Webex Calling: the operator console that was missing.
Discover a new native integration. Attendant Console is fully compatible with all Cisco platforms!
Products Blog
Voice Analytics: designed for your privacy and security.
Voice Analytics: designed for your privacy and security.
Voice Analytics handles a variety of sensitive, personal data. Learn why you can trust it to do so, any time, anywhere.


0 تعليق