Cloud, Manager Assistant, Voice Analytics: a brand-new Imagicle world.
Updated
$published_time = int(1586422826)
$modified_time = int(1627400297)
Secure Software Development Life Cycle.
Getting started with OWASP Web Security Test Guide.
- allow you to test only the exposed code;
- are performed at the end of the SDLC, so they are easily integrated into our Continuous Integration system.
Designing a Secure Software Development Life Cycle.
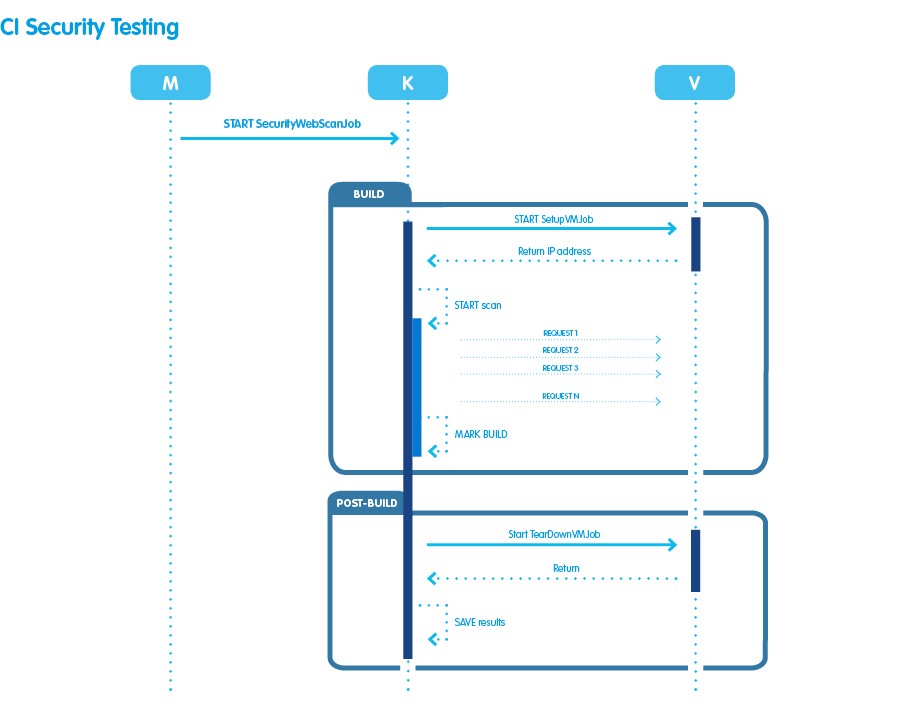
- M: Jenkins‘ master node;
- K: a new machine on which we have installed our web scanner and will be our slave node where the job that governs the scan will be performed;
- V: another Jenkins slave node where the setup and teardown jobs that will be discussed later will be performed.
- the previously prepared snapshot is restored;
- all Windows Updates are made with the necessary restarts;
- the installation of the latest package created by the master branch of our repository is launched;
- once the installation is successfully completed, the setup job communicates the IP address of the web portal.
- a first phase of „discovery“ of the web pages;
- a second phase in which the pages found are tested to check for any vulnerabilities.
- SUCCESS, if no vulnerabilities of the configured severity and confidence have been detected;
- FAILURE, if vulnerabilities have been detected.
- duplication of tests performed is avoided;
- the application is tested for a greater number of vulnerabilities;
- a test standard is created, regardless of the user’s ability.
Conclusions.
#stayimagicle
Sie könnten auch interessiert sein an...
-
Brochure IT Blog
Prova pubblicazione
Prova pubblicazione -
Entdecken Sie
BlogDE Prova Immagine
DE Prova ImmagineDE Lorem ipsum dolor sit amet, consectetur adipiscing elit. Fusce mattis eros ut nisl sollicitudin convallis. Aenean pulvinar consectetur ligula efficitur tincidunt. Nunc scelerisque nunc at leo maximus condimentum. Nulla viverra lorem id imperdiet fringilla. Donec vel vulputate nibh, id euismod nulla. Nulla elit felis, facilisis sed accumsan nec, vehicula in nisl. Quisque posuere augue […] -
Products Blog
Why You Should Choose Imagicle Virtual Agents AI to Empower Your Bank.
Why You Should Choose Imagicle Virtual Agents AI to Empower Your Bank.Discover the level of omnichannel automation Conversational AI brings to your bank.
Brochure IT Blog
Prova pubblicazione
Prova pubblicazione
 Entdecken Sie
Entdecken Sie
Blog
DE Prova Immagine
DE Prova Immagine
DE Lorem ipsum dolor sit amet, consectetur adipiscing elit. Fusce mattis eros ut nisl sollicitudin convallis. Aenean pulvinar consectetur ligula efficitur tincidunt. Nunc scelerisque nunc at leo maximus condimentum. Nulla viverra lorem id imperdiet fringilla. Donec vel vulputate nibh, id euismod nulla. Nulla elit felis, facilisis sed accumsan nec, vehicula in nisl. Quisque posuere augue […]
Products Blog
Why You Should Choose Imagicle Virtual Agents AI to Empower Your Bank.
Why You Should Choose Imagicle Virtual Agents AI to Empower Your Bank.
Discover the level of omnichannel automation Conversational AI brings to your bank.


0 Kommentare