Imagicle application security best practices
As the biggest 21st-century data breaches have taught us, cyber-attacks are costly incidents. They not only involve the financial losses and post-attack response, but also cause loss of trust and reputation (aka, loss of customer).
At Imagicle, we have long ago learned that, for our customers, the security of an application is a discriminating factor in choosing to adopt our products in the first place.
Here are some best practices we’ve put into practice to make sure not to lose anything or anyone we care about. 
Hack yourself.
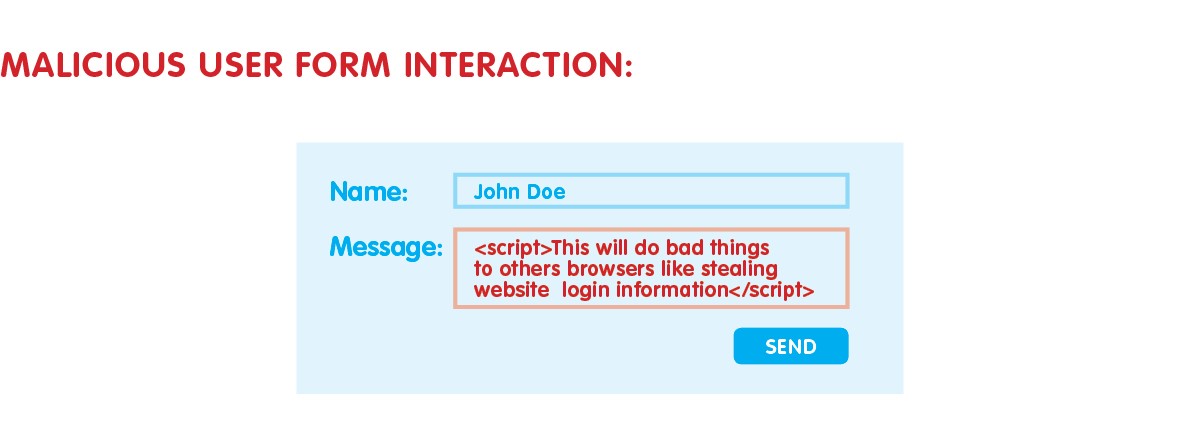
We are aware that, to protect an application, identifying known vulnerabilities may not be enough: to be able to prevent the highest possible number of attacks, it’s necessary to know in detail the ways it can be performed.
You have to identify all security issues and vulnerabilities within the application itself before a malicious hacker identifies and exploits them – which, simply put, means that an excellent way to know how to prevent an attack is trying to think of how you’d hack yourself.
Later in this post, you will find a useful tool to get some practice in.
Spread knowledge.
In general, an unsafe application exposes a company to incalculable risks, and while the big players have the resources to recover faster from such attacks, small and medium businesses may have to shut down.
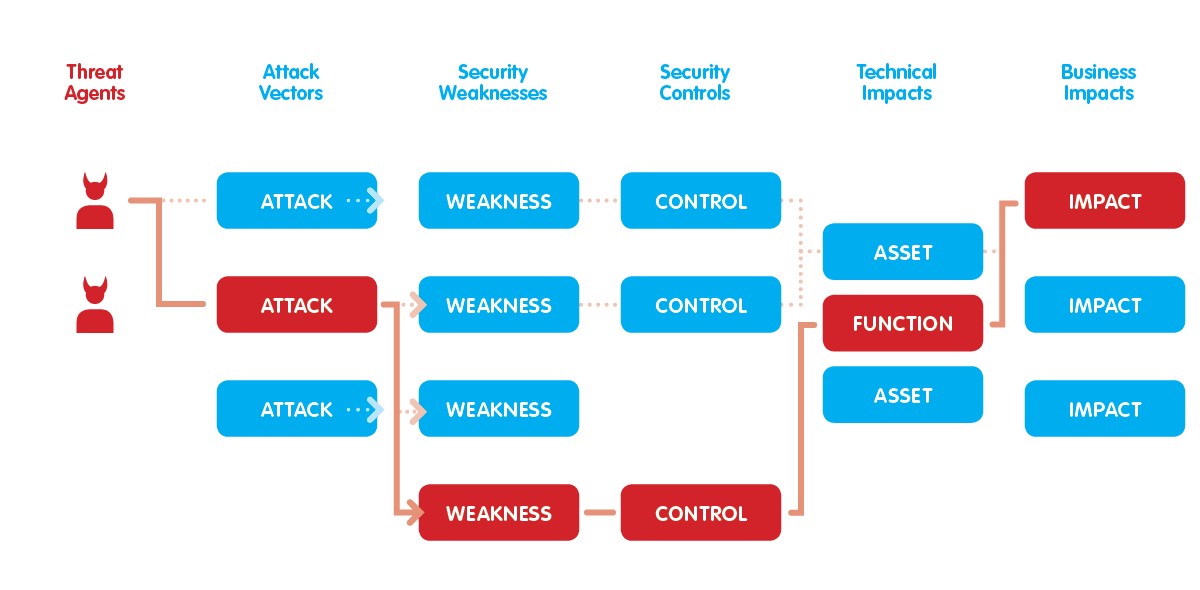
Through a technique called „Privilege escalation”, in fact, a hacker can start from a simple vulnerability to gain more and more important permissions, up to take control over a server or the entire network of a company (and by then, mate, you’re in a whole world of hurt  ).
).
In our case, we have started an internal discussion to spread the security culture and sensibility and stay informed on what is happening in the web application security industry.
Use a web vulnerability scanner.
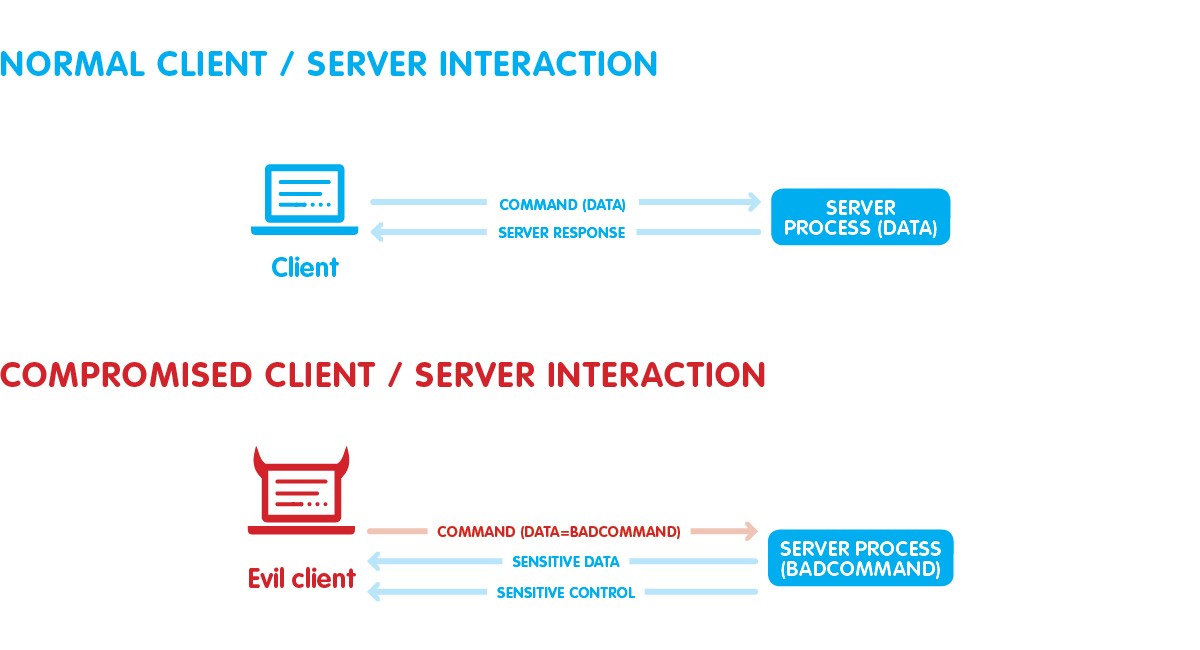
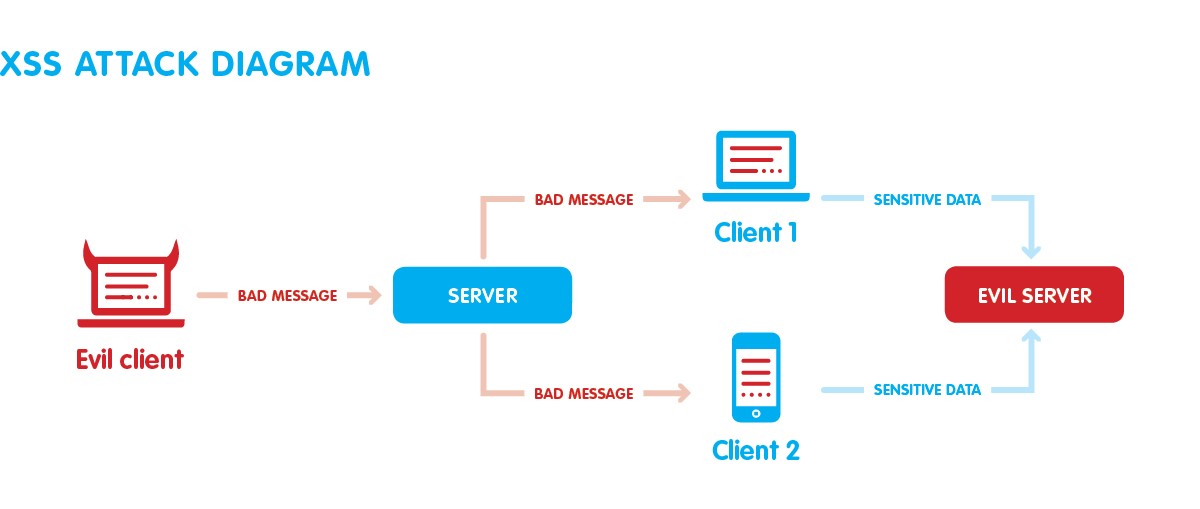
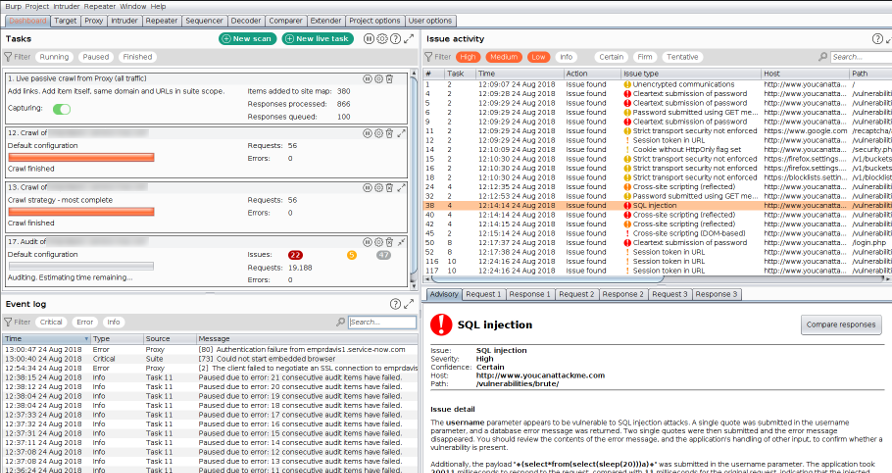
Meanwhile, we began to use the Burp suite to analyze our applications. The Burp suite is a web vulnerability scanner. It covers over 100 generic vulnerabilities, such as SQL injection and cross-site scripting (XSS), with a great performance against all vulnerabilities in the OWASP top 10.
The Burp suite covers the first 2 phases in hypothetical hacker activity: reconnaissance and scanning. The adoption of this suite helped us to identify and fix some OWASP vulnerabilities based on XSS and SQL injection, along with other low priority problems like cross-site scripting, cross-domain post, directory listing, and others.
 Matteo Conta - 15 Mai, 2019 - 9 ’ read
Matteo Conta - 15 Mai, 2019 - 9 ’ read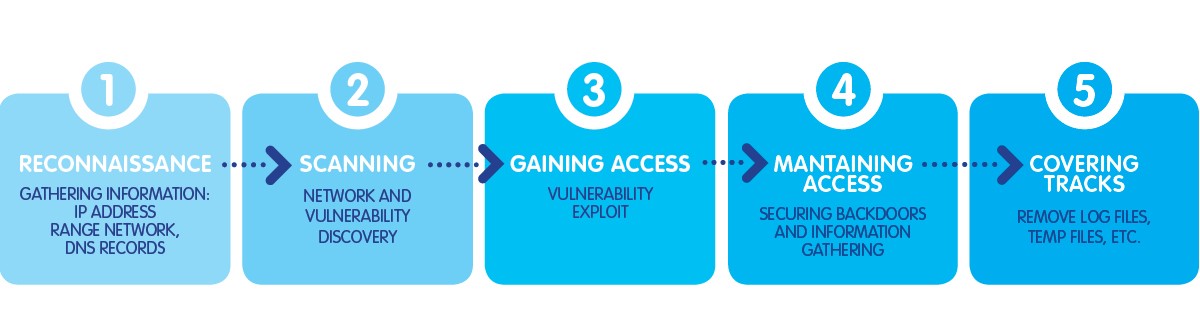
0 Kommentare