Cloud, Manager Assistant, Voice Analytics: a brand-new Imagicle world.
Updated
OAuth 2.0 support: Microsoft 365 native integration.
How many times have you had to enter your credentials again and again to access a service? Well, all this becomes a thing of the past with OAuth 2.0. Spring 2021 Release will be here soon, and this is the first of its flowers: get ready to discover OAuth 2.0, its benefit in terms of security and simplicity, and its use cases within the Imagicle UCX Suite.
What is OAuth 2.0?
2.0
How OAuth 2.0 works.
OAuth 2.0 defines four roles:
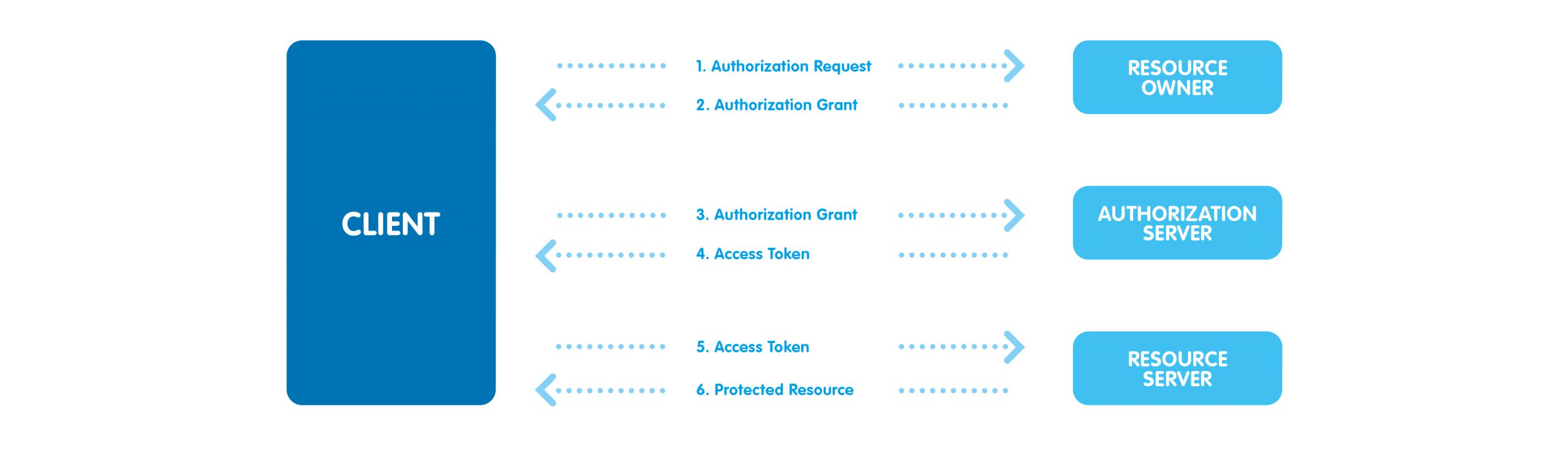
What makes OAuth 2.0 more secure.
OAuth 2.0, with respect to Basic Auth, brings a lot of advantages:
- relies on SSL to ensure data;
OAuth 2.0 in the Imagicle UCX Suite.
Features that currently support it are:
- Digital Fax’s Email to Fax
- Calendar integration in Attendant Console
Let’s look specifically at how individual services leverage this integration.
Email to Fax.

Calendar integration.
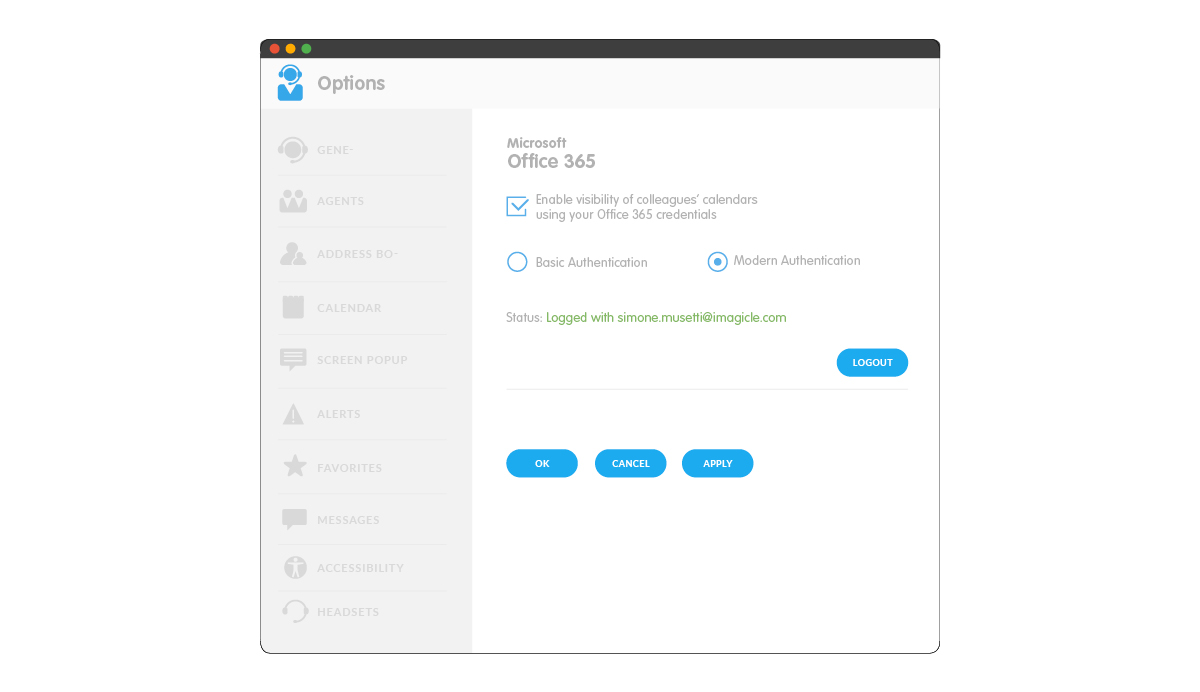
Conclusions.
También podría interesarle...
-
Brochure IT Blog
Prova pubblicazione
Prova pubblicazione -
Descubra
BlogES Prova Immagine
ES Prova ImmagineES Lorem ipsum dolor sit amet, consectetur adipiscing elit. Fusce mattis eros ut nisl sollicitudin convallis. Aenean pulvinar consectetur ligula efficitur tincidunt. Nunc scelerisque nunc at leo maximus condimentum. Nulla viverra lorem id imperdiet fringilla. Donec vel vulputate nibh, id euismod nulla. Nulla elit felis, facilisis sed accumsan nec, vehicula in nisl. Quisque posuere augue […] -
Products Blog
Why You Should Choose Imagicle Virtual Agents AI to Empower Your Bank.
Why You Should Choose Imagicle Virtual Agents AI to Empower Your Bank.Discover the level of omnichannel automation Conversational AI brings to your bank.
Brochure IT Blog
Prova pubblicazione
Prova pubblicazione
 Descubra
Descubra
Blog
ES Prova Immagine
ES Prova Immagine
ES Lorem ipsum dolor sit amet, consectetur adipiscing elit. Fusce mattis eros ut nisl sollicitudin convallis. Aenean pulvinar consectetur ligula efficitur tincidunt. Nunc scelerisque nunc at leo maximus condimentum. Nulla viverra lorem id imperdiet fringilla. Donec vel vulputate nibh, id euismod nulla. Nulla elit felis, facilisis sed accumsan nec, vehicula in nisl. Quisque posuere augue […]
Products Blog
Why You Should Choose Imagicle Virtual Agents AI to Empower Your Bank.
Why You Should Choose Imagicle Virtual Agents AI to Empower Your Bank.
Discover the level of omnichannel automation Conversational AI brings to your bank.


0 comentarios